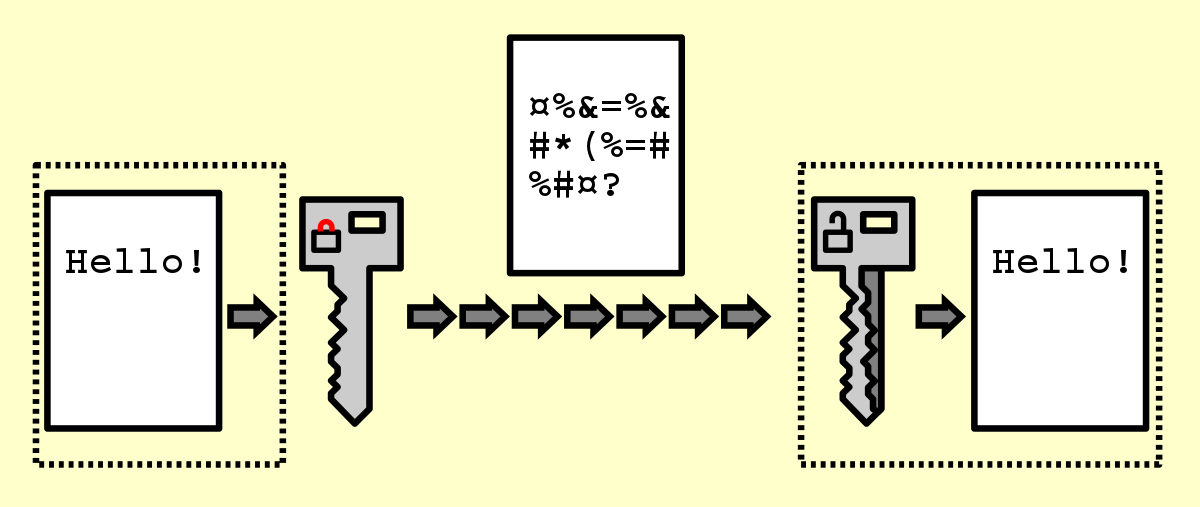
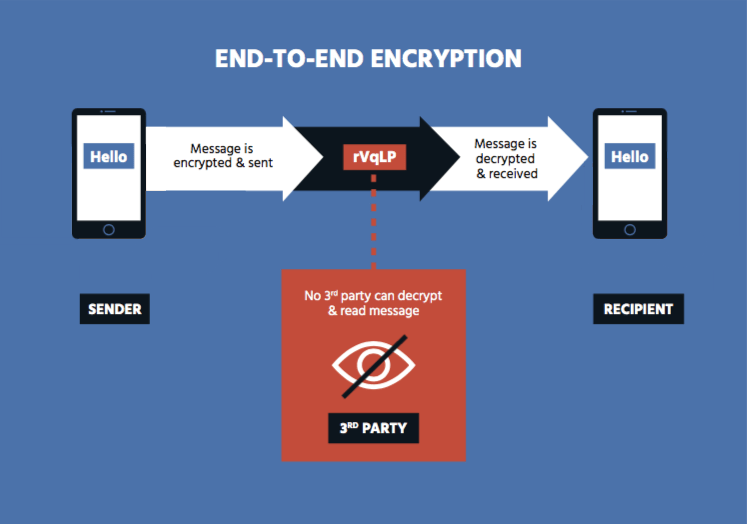
GitHub - magiclen/js-short-crypt: ShortCrypt is a very simple encryption library, which aims to encrypt any data into something random at first glance.

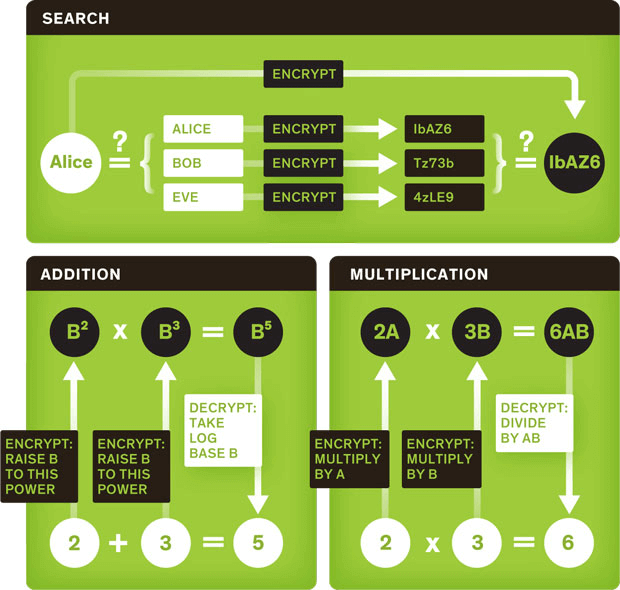
Remote Sensing | Free Full-Text | CGAN BeiDou Satellite Short-Message- Encryption Scheme Using Ship PVT

Remote Sensing | Free Full-Text | CGAN BeiDou Satellite Short-Message- Encryption Scheme Using Ship PVT


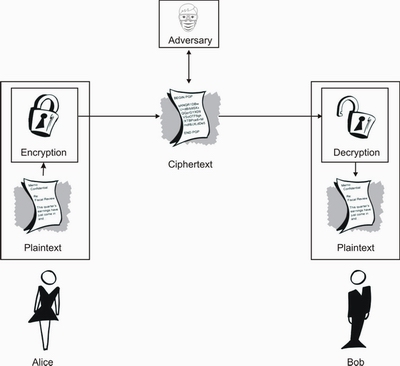



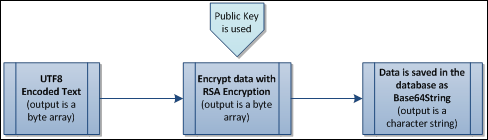


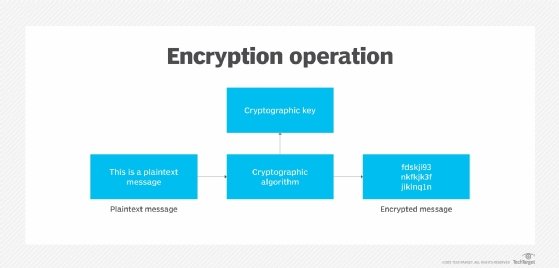

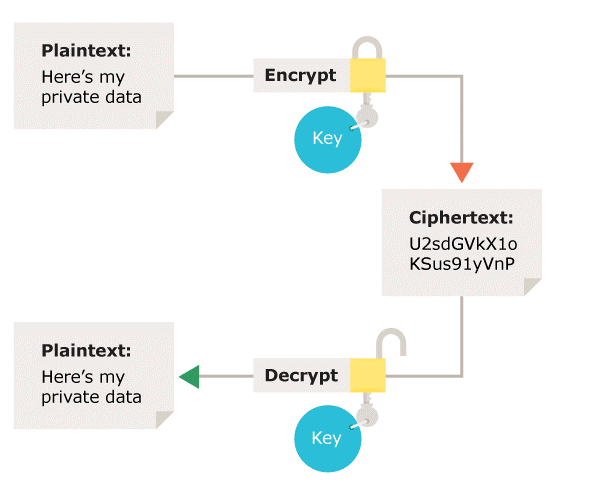

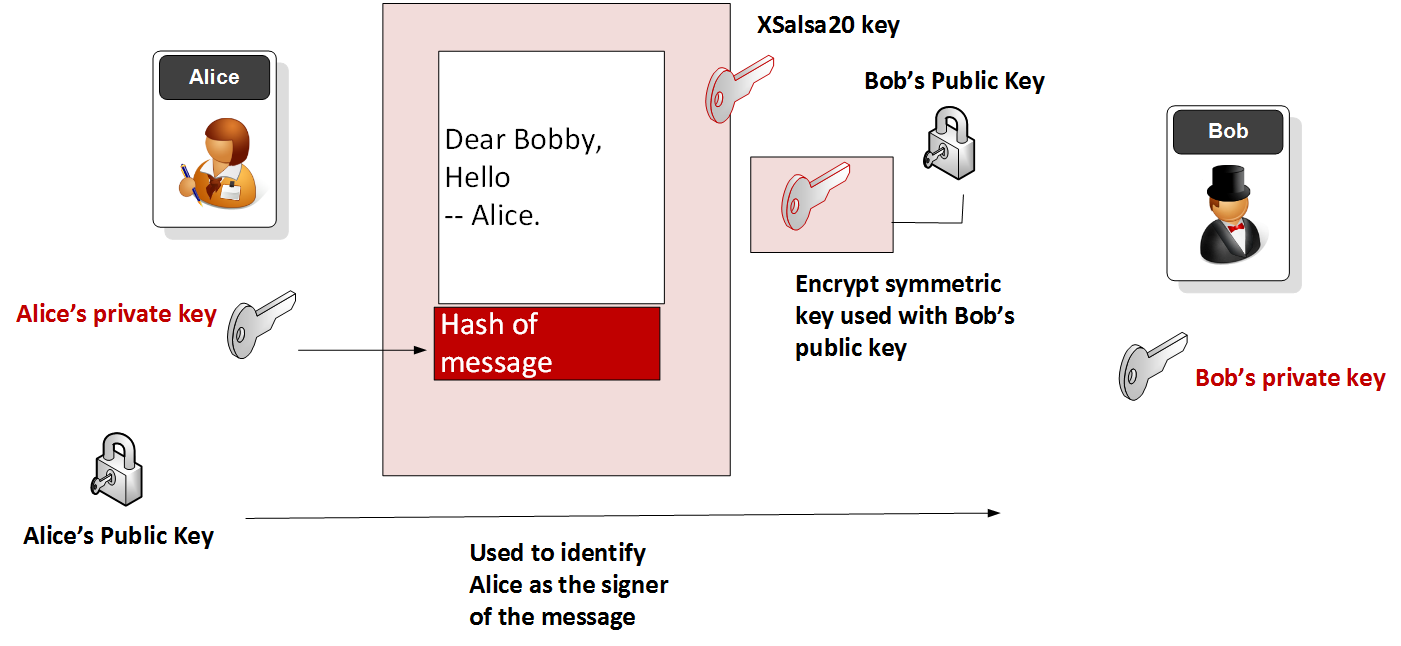



![PDF] Fast Keyword Search over Encrypted Data with Short Ciphertext in Clouds | Semantic Scholar PDF] Fast Keyword Search over Encrypted Data with Short Ciphertext in Clouds | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ac4bf8ba86231775f88e22f844392501fa337403/4-Figure1-1.png)